Enabling logging in API Gateway for your stage is fairly easy. You go into the Console, setup a role for API Gateway to
use for logging, find the stage and enable logs. It will enable logging for all methods within that stage. Doing the
same configuration using CloudFormation is not completely obvious though, as
the stage object’s MethodSettings
property seems to allow you to only do that for a specific resource and method.
In short, this is what we are trying to accomplish within the settings for the whole Stage:
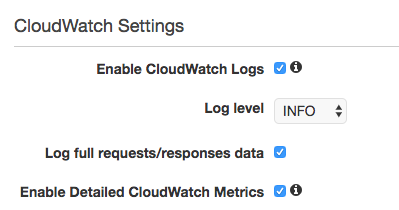
MethodSetting
in CloudFormation requires a specific ResourcePath and HttpMethod, which seems to suggest, you need to specify those
properties for every path and method in your API. Luckily, that’s not entirely true. While you can use this property for
a very specific resource and method, you can also use it for ALL resources and method.
To do that, using troposphere, you can specify it like this:
| |
or directly in JSON:
| |
In order for that to work, you also need to create a Role for API Gateway to write to logs and let API Gateway know what that role is:
| |
You only have to set the above once (i.e. in one CloudFormation stack in a region within your AWS account), as the API Gateway account setting is global for the whole region.


